Kerberos authentication and tickets Tutorial Example December 2019
This event generates every time Key Distribution Center issues a Kerberos Ticket Granting Ticket (TGT). This event generates only on domain controllers. If TGT issue fails then you will see Failure event with Result Code field not equal to " 0x0 ". This event doesn't generate for Result Codes: 0x10 and 0x18.
Daren Matthews » How Kerberos Works
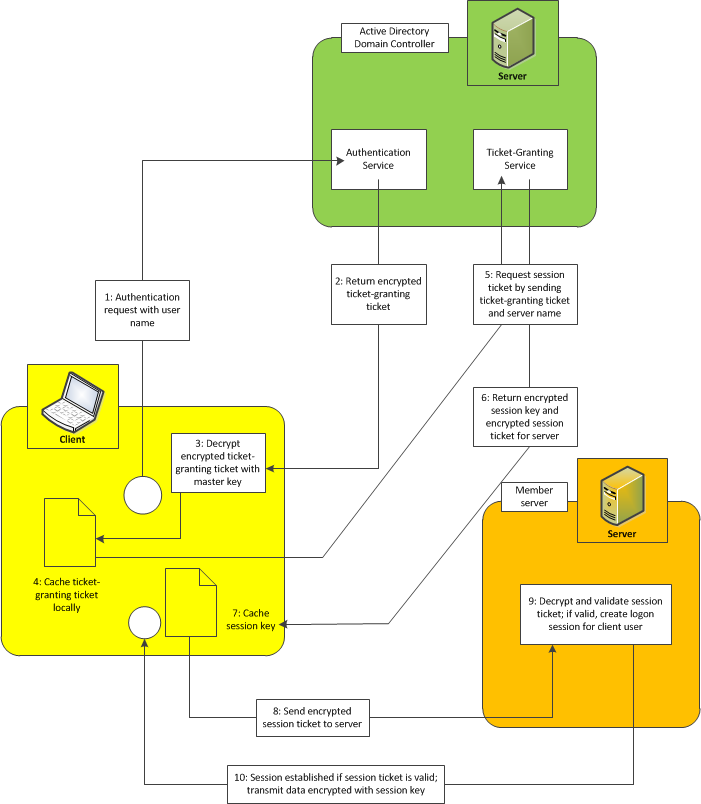
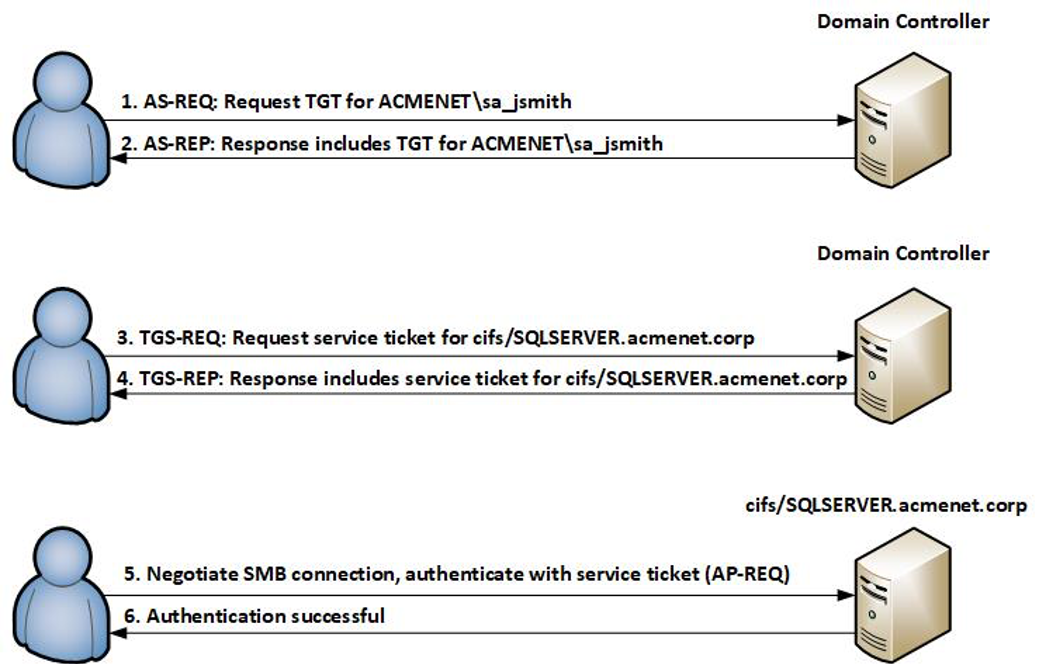
In summary, the authentication flow is as follows: The user is authenticated with Active Directory over Kerberos and has a Ticket Granting Ticket (TGT) stored locally on the workstation. The user makes a request from the browser to access the web application. The web application redirects the browser to Red Hat's SSO.

Kerberos Authentication What It Is & How It Works BMC Software Blogs
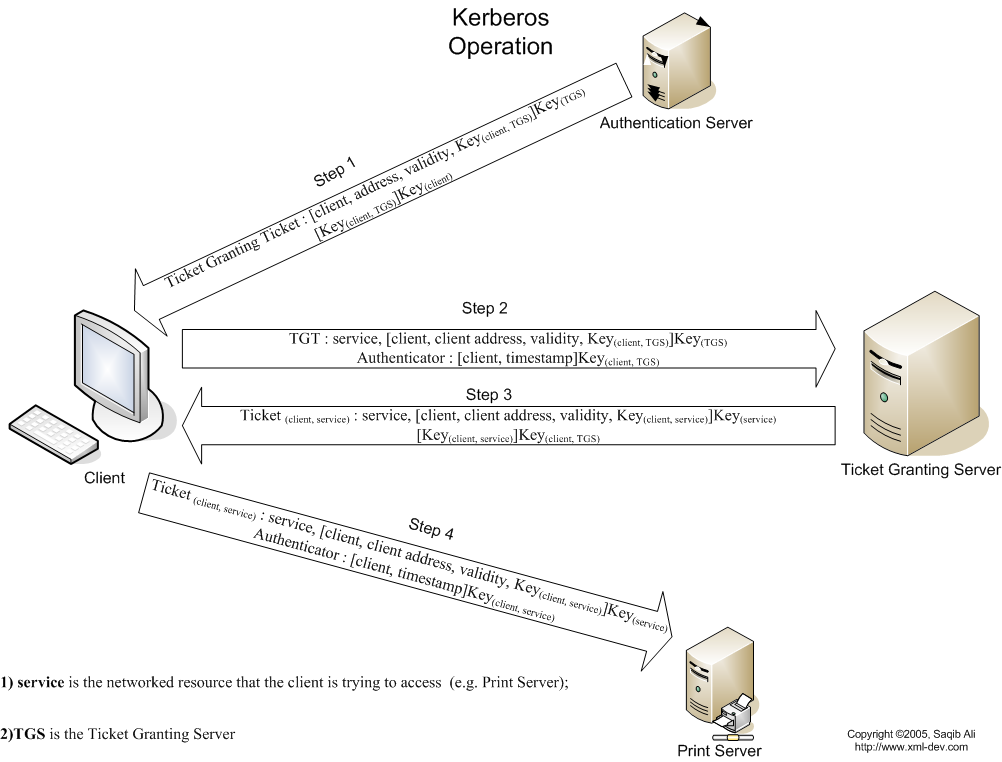
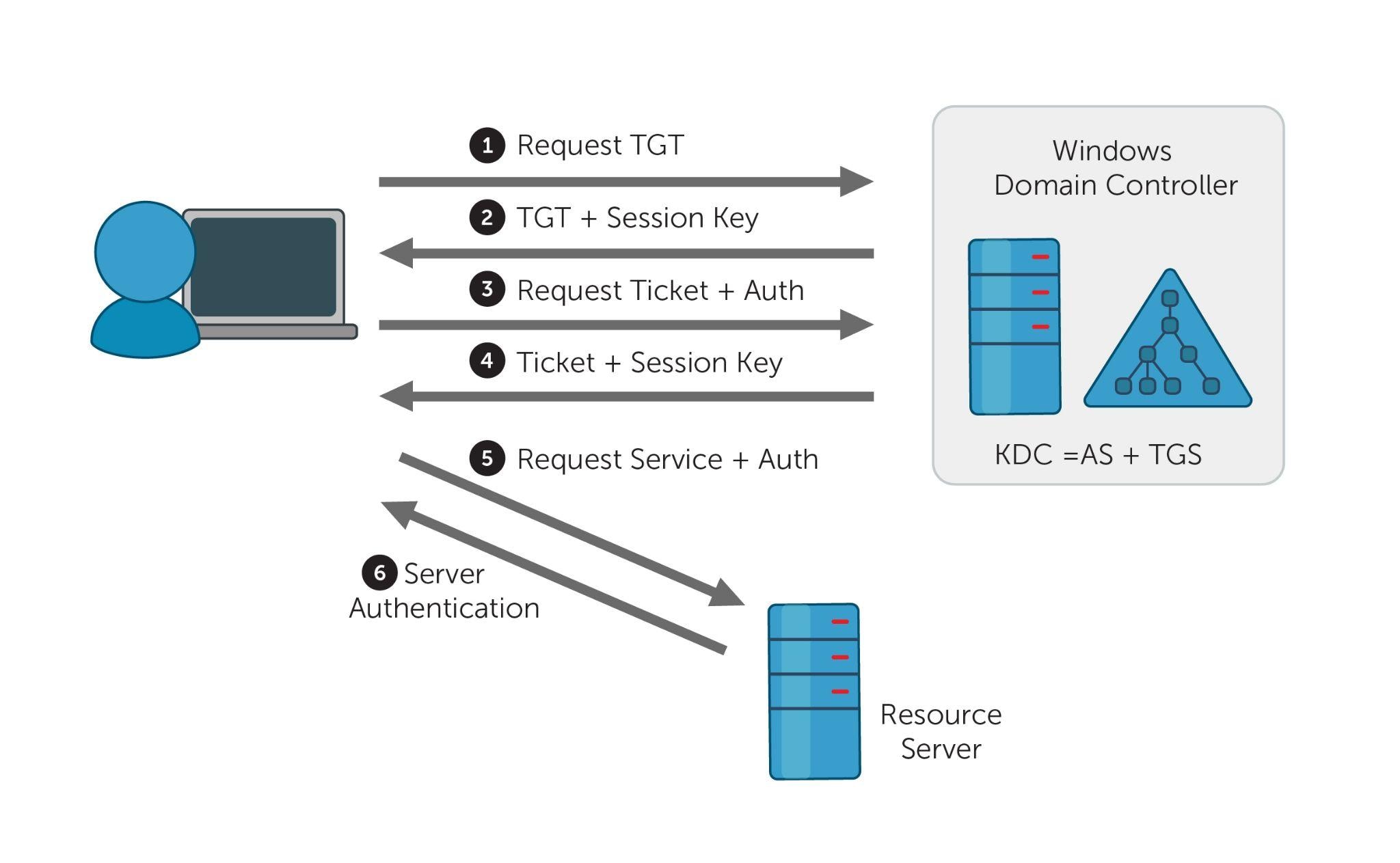
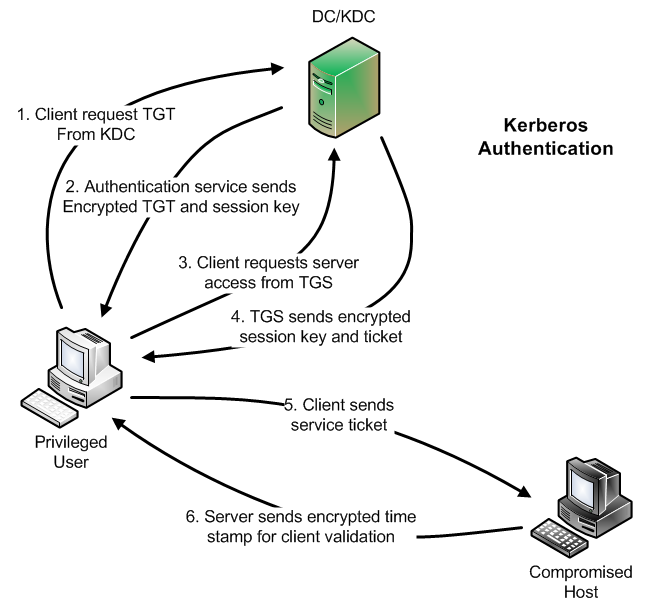
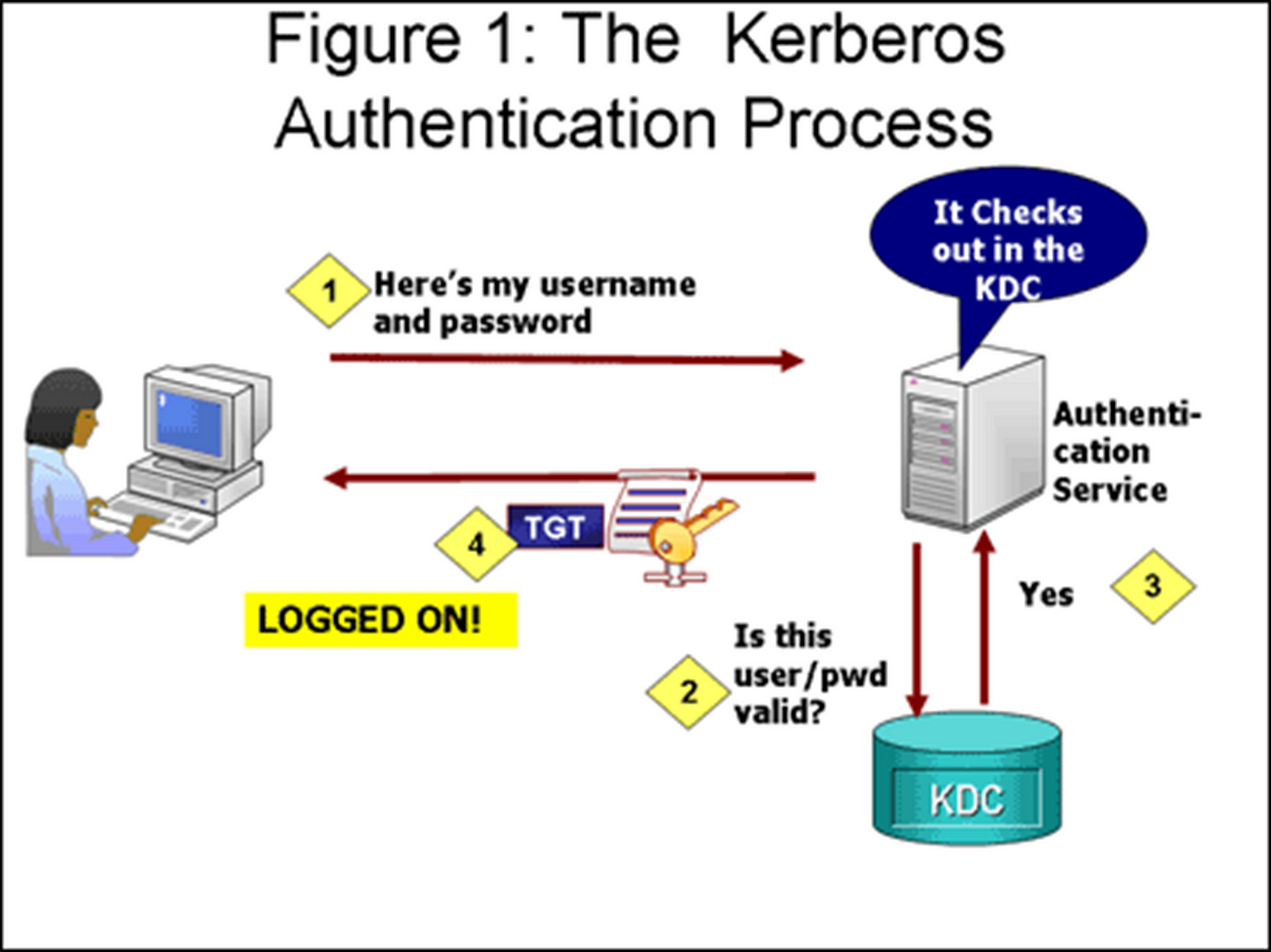
These are the steps in Kerberos Authentication: PC Client logs on the domain. A Ticket-Granting Ticket (TGT) request is sent to a Kerberos KDC The Kerberos KDC returns a TGT and a session key to the PC Client A ticket request for the application server is sent to the Kerberos KDC. This request consists of the PC Client, TGT and an authenticator.

Kerberos PassTheTicket Basics YouTube
Initial Client Authentication Request- The protocol flow starts with the client logging in to the domain. In this step, the user asks for the TGT or authentication token from the AS. The TGT request is sent to the Kerberos KDC. Verification of Client Credentials- The KDC must verify the user's credentials to send an encrypted session key and.
Detecting the Kerberos noPac Vulnerabilities with Cortex XDR™ Palo Alto Networks Blog
1 Since May, our reporting tools are showing lots of failed authentication attempts against some of our DCs, for an account named host (which does not exist). Event Viewer shows those failures as ID 4768 events: A Kerberos authentication ticket (TGT) was requested.
Kerberos Authentication Architecture dhaverkate
Adversaries may abuse a valid Kerberos ticket-granting ticket (TGT) or sniff network traffic to obtain a ticket-granting service (TGS) ticket that may be vulnerable to Brute Force. [1] [2] Service principal names (SPNs) are used to uniquely identify each instance of a Windows service.

Active Directory Authentication methods How do Kerberos and NTLM work Learn [Solve IT]
Figure 1. Kerberos authentication protocol Event ID 4768 (S) — Authentication Success In cases where credentials are successfully validated, the domain controller (DC) logs this event ID with the Result Code equal to "0x0" and issues a Kerberos Ticket Granting Ticket (TGT) (Figure 1, Step 2). Event ID 4768 (F) — Authentication Failure
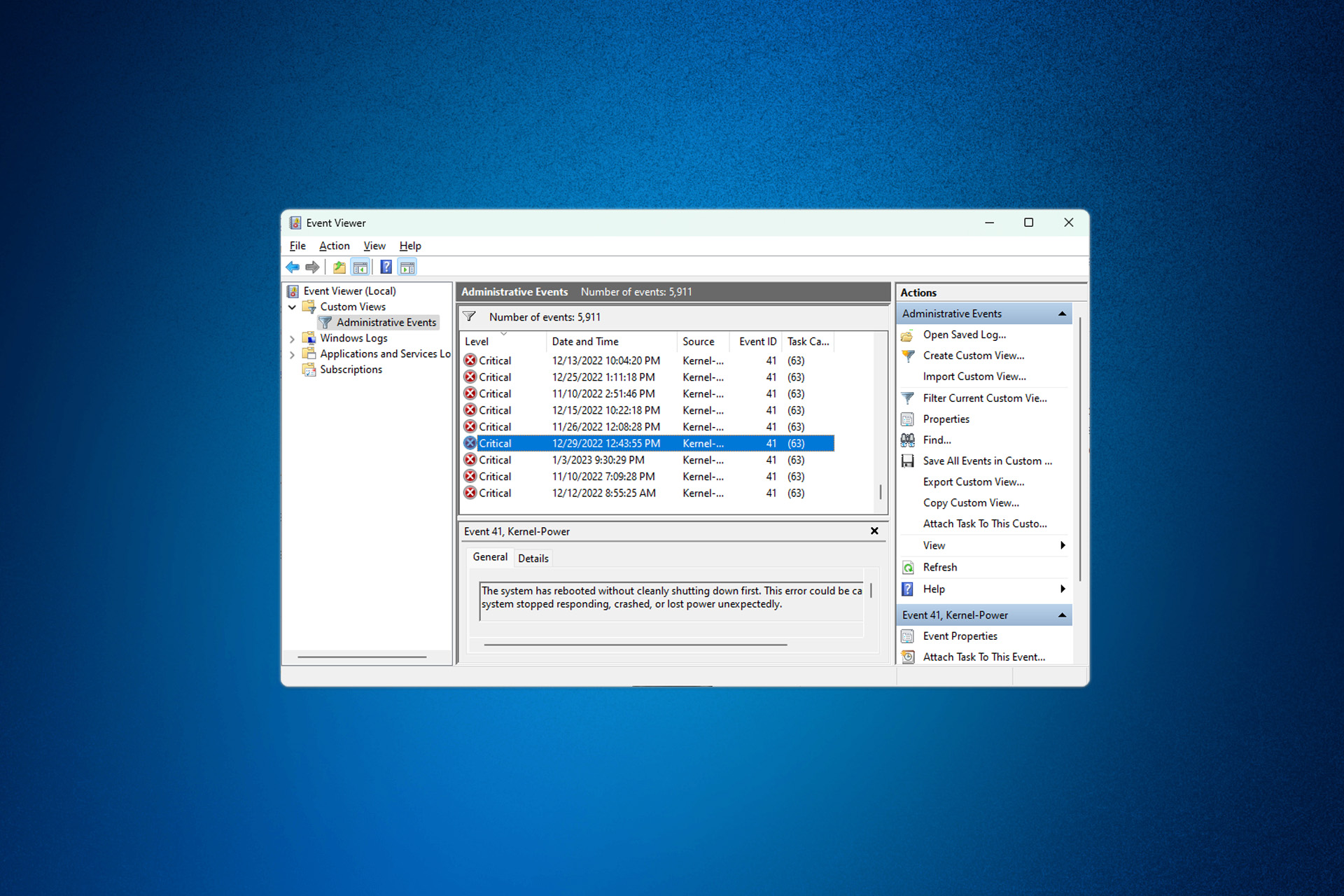
Fix Event ID 4768 Kerberos Authentication Ticket Requested
A Kerberos authentication ticket (TGT) was requested.Account Information: Account Name: %1 Supplied Realm Name: %2 User ID: %3Service Information: Service Name: %4 Service ID: %5Network Information: Client Address: %10 Client Port: %11Additional Information: Ticket Options: %6 Result Code: %7 Ticket Encryption Type: %8 Pre-Authentication Type: %9Certificate Information:
Kerberos Tickets on Linux Red Teams Mandiant
4768: A Kerberos authentication ticket (TGT) was requested On this page Description of this event Field level details Examples Discuss this event Mini-seminars on this event This event is logged on domain controllers only and both success and failure instances of this event are logged.

Kerberos Authentication Process
Event ID - 4768. A Kerberos authentication ticket (TGT) was requested. This event is logged when a computer in the domain needs to authenticate to the DC typically when a workstation boots up or a server restarts. In these instances, you'll find a computer name in the User Name and fields. Computer generated kerberos events are always.
Kerberos Authentication Failed / 4768(S, F) A Kerberos authentication ticket (TGT) was
Oct 22nd, 2018 at 3:20 AM. 4768 - The event will generate when user logon or some applications which need Kerberos authentication. Refer to this article to troubleshoot Event ID 4768 - A Kerberos authentication ticket (TGT) was requested. Audit the successful or failed logon and logoff attempts in the network using the audit policies: https.
Brief Summary of Kerberos. Kerberos authentication process. by Mahbuba Shahrin Mar, 2022
4768(S, F): A Kerberos authentication ticket (TGT) was requested. \n. Applies to \n \n; Windows 10 \n; Windows Server 2016 \n \n \n. Subcategory: Audit Kerberos Authentication Service \n. Event Description: \n. This event generates every time Key Distribution Center issues a Kerberos Ticket Granting Ticket (TGT). \n. This event generates only.
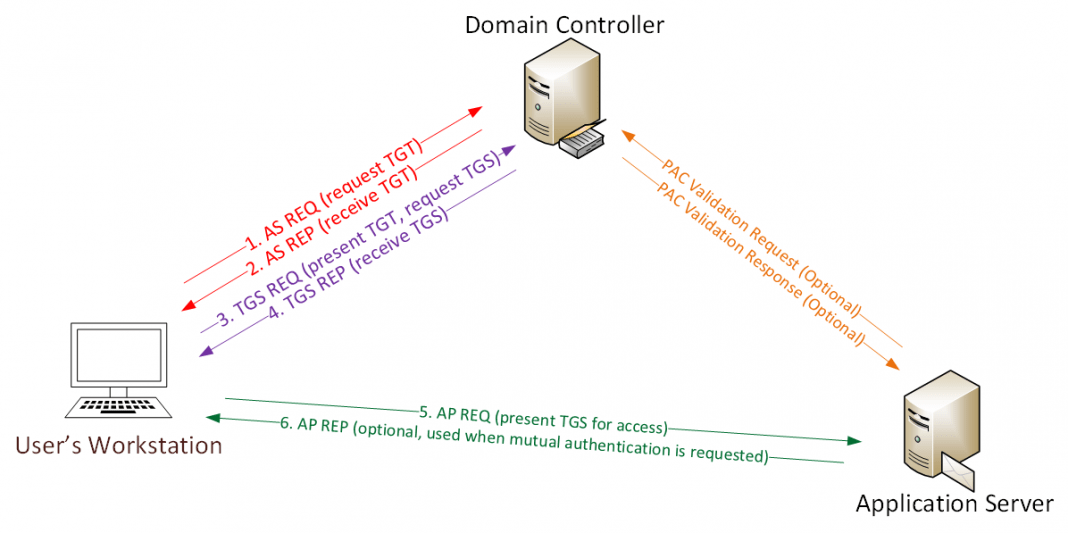
Defending and Preventing Against Active Directory Kerberos Attacks Security Investigation
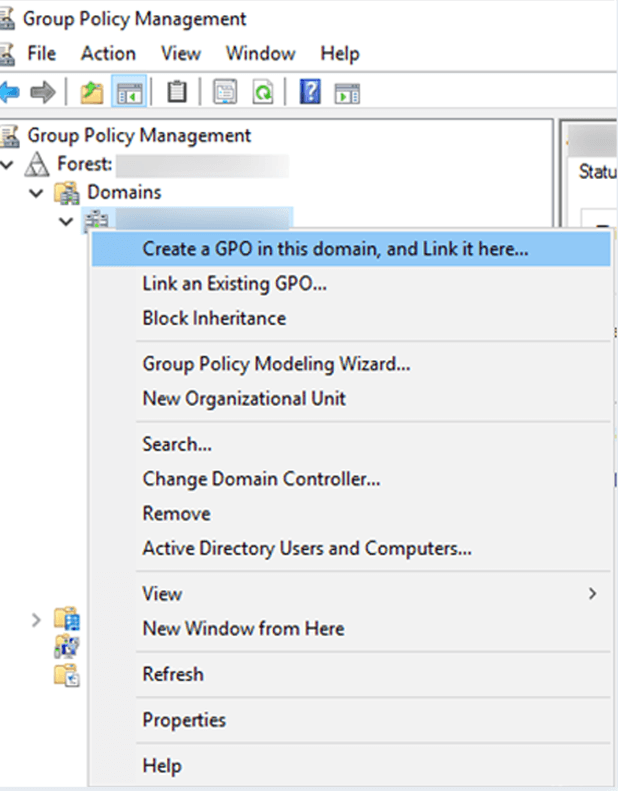
Follow the below steps to enable Active Directory Kerberos Logon Audit event 4768 via Default Domain Controllers Policy. 1. Press the key ' Window' + ' R'. 2. Type the command gpmc.msc, and click OK. Note: Skip the above steps by clicking Start ->Administrative Tools ->Group Policy Management. 3. Expand the domain node and Domain.
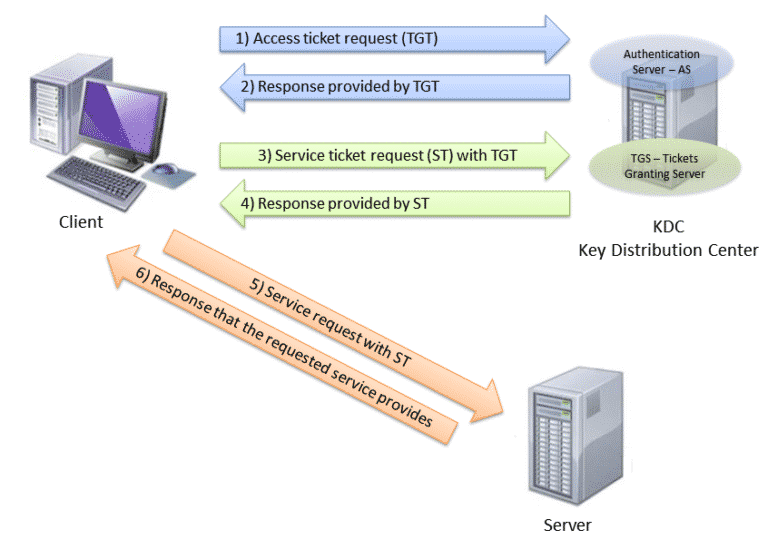
Kerberos Diego Calvo
Pythonic Ntsecapi. The main purpose of adding SSPI features to the Impacket library is to efficiently re-use the current AD context in a classic Windows Single Sign-On style, eliminating the need to manually specify the target credential material to be used. Introduced in Certipy 4.0, the sspi part is intended to achieve the same goal: Now.

4768(S, F) A Kerberos authentication ticket (TGT) was requested. (Windows 10) Windows security
Essentially, a TGT is proof of successful user authentication, usually by password. Kerberos authentication scheme. Source: https://en.wikipedia.org/wiki/Kerberos_ (protocol) However, there is a way to get a TGT without knowing the password — using a certificate.

How Does Kerberos Work? The Authentication Protocol Explained
Step 1. Extract the TGT. To perform a pass-the-ticket attack with Rubeus, the first step is to obtain a TGT. TGTs and NTLM hashes may or may not be stored on a system after a user logs off, based on security settings.